Wireguard, why won’t it work?
Hey guys!
I have been working on setting up a WireGuard tunnel between my server that is on my LAN to my VPS hosted at https://ionos.com.
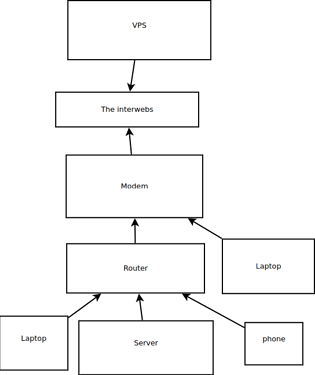
The LAN server which from here on I will refer to as (the) server, runs Ubuntu Server 20.04. It lives behind my router which is in turn behind a modem. I hope this will help:
The VPS which I will call (the) VPS is also running Ubuntu Server 20.04.
The end goal of this is to send web pages through the tunnel and serve them on the VPS. The issue is that for some reason, after setting the tunnel up it doesn’t connect.
What I did
I ran the following commands on both the VPS and the Server
1. Set openresolv to do DNS
sudo apt install openresolv sudo reboot
2. Create the keys.
sudo -i cd /etc/wireguard/ umask 077 wg genkey | tee privatekey | wg pubkey > publickey
3. Make some config files
This was the config file for the VPS aka the ‘host’ of the VPN
[Interface] #VPS PrivateKey=the-generated-private-key-for-the-VPS Address=10.252.0.1/32 DNS=8.8.8.8 ListenPort = 51820 [Peer] #Server PublicKey=the-generated-public-key-for-the-server AllowedIPs=10.252.0.2/32
This was the config file for the Server aka the ‘client’ of the VPN
[Interface] #server PrivateKey=the-generated-private-key-for-the-server Address=10.252.0.2/32 DNS=8.8.8.8 ListenPort = 51820 [Peer] #VPS PublicKey=the-generated-public-key-for-the-VPS Endpoint=the-VPS-ip:51820 AllowedIPs=0.0.0.0/0, ::/0
4. Start the service on the VPS
systemctl start wg-quick@wg0
5. Start the VPN on the Server
sudo wg-quick up wg0
Which returned
[#] ip link add wg0 type wireguard [#] wg setconf wg0 /dev/fd/63 [#] ip -4 address add 10.252.0.2/32 dev wg0 [#] ip link set mtu 1420 up dev wg0 [#] resolvconf -a wg0 -m 0 -x [#] wg set wg0 fwmark 51820 [#] ip -6 route add ::/0 dev wg0 table 51820 [#] ip -6 rule add not fwmark 51820 table 51820 [#] ip -6 rule add table main suppress_prefixlength 0 [#] ip6tables-restore -n [#] ip -4 route add 0.0.0.0/0 dev wg0 table 51820 [#] ip -4 rule add not fwmark 51820 table 51820 [#] ip -4 rule add table main suppress_prefixlength 0 [#] sysctl -q net.ipv4.conf.all.src_valid_mark=1 [#] iptables-restore -n
Then I start pinging around to see what I could find
On the Server:
ping -c 3 10.252.0.1 PING 10.252.0.1 (10.252.0.1) 56(84) bytes of data. --- 10.252.0.1 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2024ms
ping -c 3 10.252.0.2 PING 10.252.0.2 (10.252.0.2) 56(84) bytes of data. 64 bytes from 10.252.0.2: icmp_seq=1 ttl=64 time=0.044 ms 64 bytes from 10.252.0.2: icmp_seq=2 ttl=64 time=0.040 ms 64 bytes from 10.252.0.2: icmp_seq=3 ttl=64 time=0.062 ms --- 10.252.0.2 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2032ms rtt min/avg/max/mdev = 0.040/0.048/0.062/0.009 ms
ip route ls default via 192.168.1.1 dev enp2s0 proto static 172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1 192.168.1.0/24 dev enp2s0 proto kernel scope link src 192.168.1.30
On the VPS
ping -c 3 10.252.0.2 PING 10.252.0.2 (10.252.0.2) 56(84) bytes of data. From 10.252.0.1 icmp_seq=1 Destination Host Unreachable ping: sendmsg: Destination address required From 10.252.0.1 icmp_seq=2 Destination Host Unreachable ping: sendmsg: Destination address required From 10.252.0.1 icmp_seq=3 Destination Host Unreachable ping: sendmsg: Destination address required --- 10.252.0.2 ping statistics --- 3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2056ms
ping -c 3 10.252.0.2 PING 10.252.0.2 (10.252.0.2) 56(84) bytes of data. From 10.252.0.1 icmp_seq=1 Destination Host Unreachable ping: sendmsg: Destination address required From 10.252.0.1 icmp_seq=2 Destination Host Unreachable ping: sendmsg: Destination address required From 10.252.0.1 icmp_seq=3 Destination Host Unreachable ping: sendmsg: Destination address required --- 10.252.0.2 ping statistics --- 3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2038ms
ip route ls default via 10.255.255.1 dev ens192 10.252.0.2 dev wg0 scope link 10.255.255.1 dev ens192 scope link
I don’t know what to test or troubleshoot next.
I do know that when I wg-quick up wg0 on the server I can no longer access the internet. I can access the LAN though.
If anyone has any help or advice they could give it would be highly appreciated!
Thank’s in advance, ComputerKid
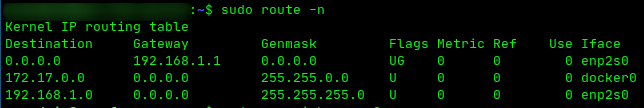 Shouldn’t wg0 be there? I just ran
Shouldn’t wg0 be there? I just ran